Introduction
Hi all, Hope everyone is good and doing well. In this blog we gonna look at one awesome framework which is really helpful in Dynamic Runtime Analysis in Android Application Pentesting.
The Drozer (Link to Download) is application assessment framework for android created by MWR InfoSecurity. It is written in iPython and has modules to exploit android vulnerabilities such as Leaking Content Providers, LFI, Various Vulnerability Scanners, Reverse Shell etc.
We can also write our own modules to automate, exploit things in android applications.
To getting started with Drozer just install on your system and drozer-agent on android device then we need to do port forwarding to connect with drozer-agent. For port forwarding you can use adb forward tcp:31415 tcp:31415 command. By default Drozer use 31415 port so in my case I’m gonna use the same.
After forwarding port, enter drozer console connect to connect drozer server to drozer agent which is installed on android device.
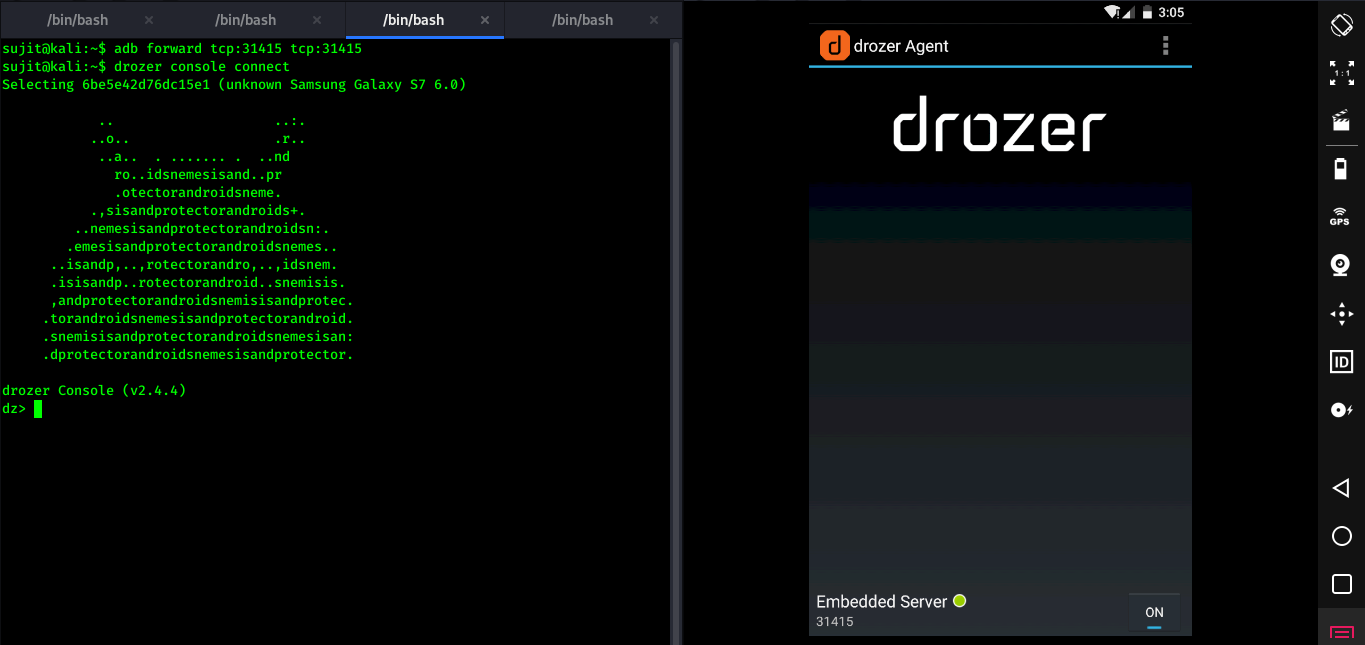
PS. In my case I’m going to use multiple vulnerable applications such as DIVA, InsecureBank etc.
This blog is meant for educational purposes only.
Basics of Drozer
Drozer has various collection of modules which are really helpful in Android Pentesting. To list down all modules of drozer just enter ls or list command.
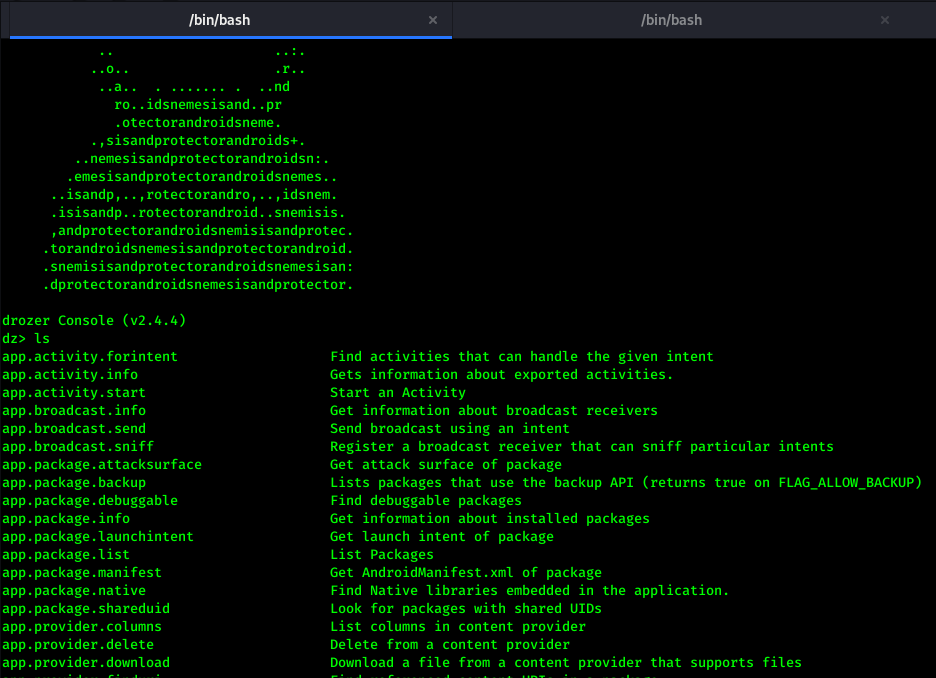
Let’s go through below modules and see what they does exactly.
app.package.list
This module is used to get all applications (packages) installed on android device. It will show you package names along with application names.
Command : run app.package.list
To find particular application we can use -f argument along with application name.
Command : run app.package.list -f insecure
app.package.attacksurface
The app.package.attacksurface module gives attack surface about particular android application in which it shows exported activities, broadcast receivers, content providers and services.
Command : run app.package.attacksurface com.android.insecurebankv2
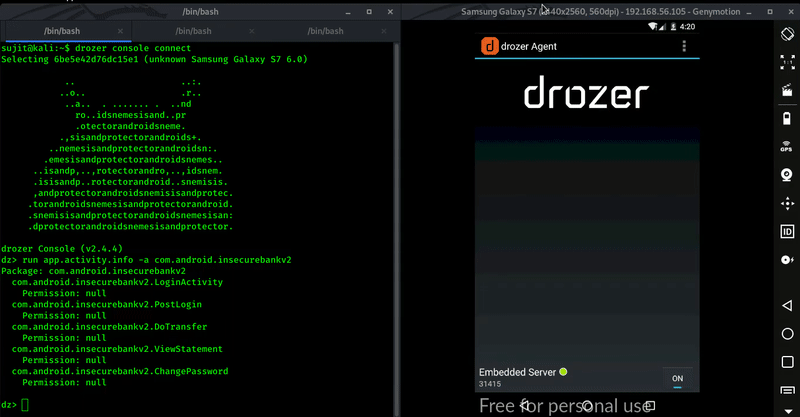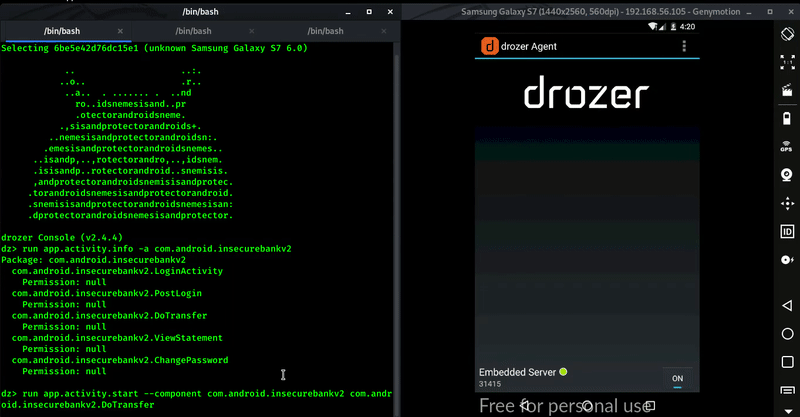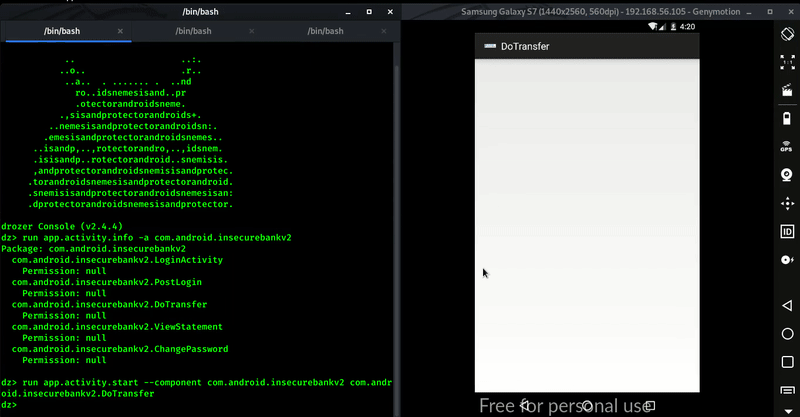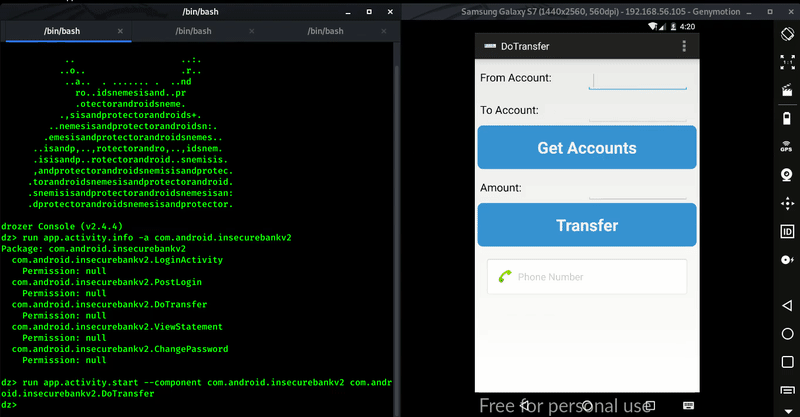
app.activity.info
This module shows exported activities which can be vulnerable.
Command : run app.activity.info -a com.android.insecurebankv2
To check if the activity is vulnerable, We can use below command.
Command : run app.activity.start –component com.android.insecurebankv2 com.android.insecurebankv2.DoTransfer
Thanks for reading this writeup and all suggestions are welcome.